Redefining Noise in DAST
The False Positive Fetish and the Forgotten Real Problem
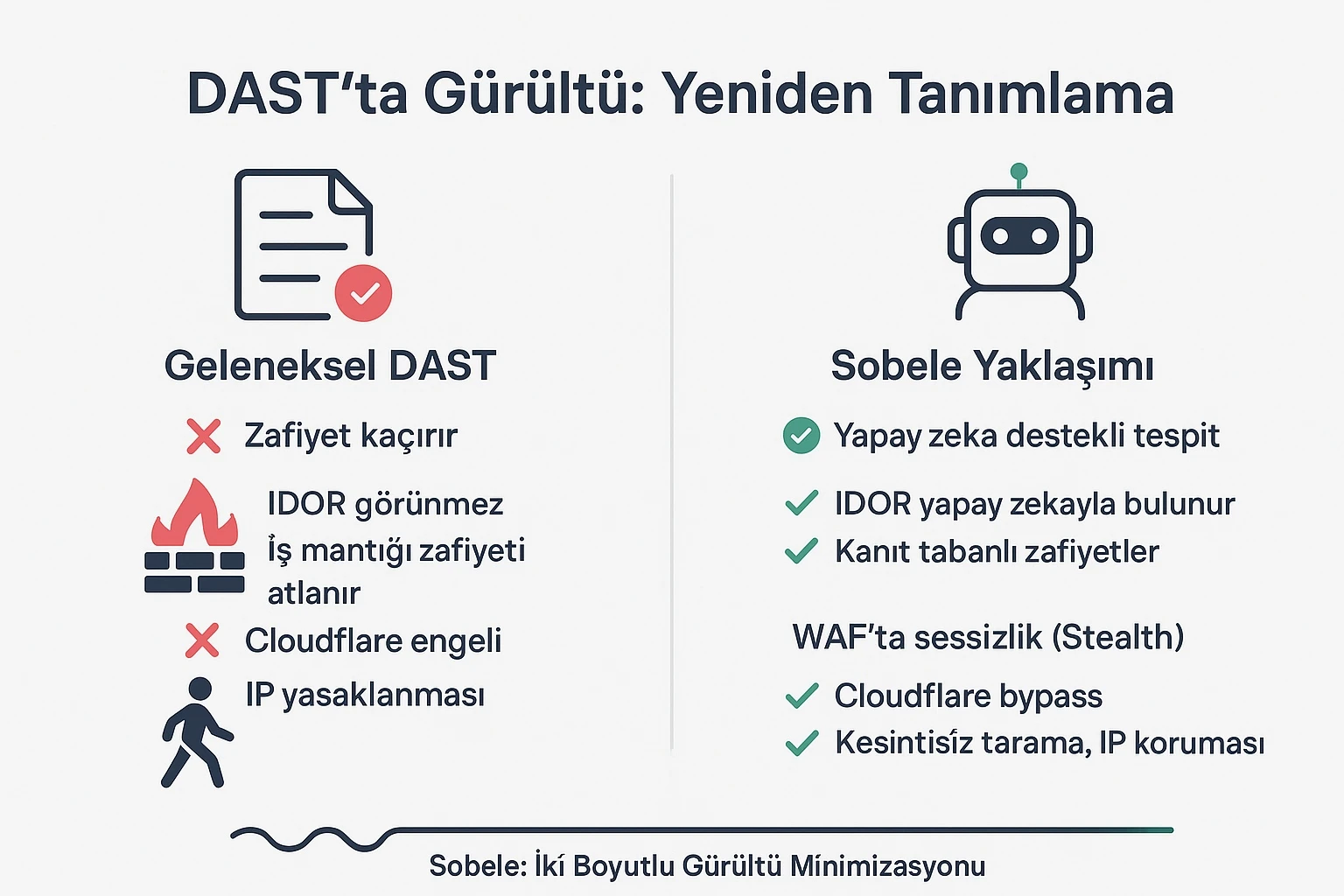
In the cybersecurity industry, certain concepts are repeated so often that they eventually transform into dogma that prevents critical thinking. The claim "we don't produce false positives" is an example of such a mantra in today's DAST (Dynamic Application Security Testing) market. While established firms like Invicti market themselves with slogans like "100% SIGNAL, 0% NOISE" in their logos, the question of where the real noise actually occurs has never been asked.
But does "noise" really only mean false positives? Why are silence and undetectability so important in web application security testing? And most importantly: is it wise to miss real vulnerabilities at the cost of avoiding false positives?
Two Major Fallacies of the Traditional Approach
1. False Positive Phobia: Sacrificing Real Vulnerabilities
Enterprise DAST tools adopt an overly conservative approach to reduce false positive rates. However, the cost of this approach is overlooked: false negatives - security vulnerabilities that exist but cannot be detected.
Invicti's difficulties in detecting critical vulnerability types like IDOR (Insecure Direct Object Reference) are clear indicators of this. Complex scenarios such as parameter manipulation, object reference analysis, and privilege escalation testing are completely abandoned out of concern for "not producing false positives."
What's the result? A clean report, but a hollow security assessment. Attackers know these gaps and exploit them.
2. The Forgotten Real Noise: Chaos on the WAF Side
The real noise produced by DAST tools appears not in the scan report, but in the Web Application Firewall (WAF) logs of the target system. Traditional scanners:
- Receive thousands of 403 Forbidden responses
- Trigger countless suspicious request notifications in the WAF
- Bombard security teams with false alarms
- Sometimes lead to IP bans and completely halt the scan
This situation causes serious problems, especially in production environments:
- SOC teams are overwhelmed with unnecessary alerts
- Business continuity is affected (automatic blocking mechanisms)
- Penetration tests are detected and defense teams spring into action
Yet real-world attackers don't behave this way. Attackers stay hidden, bypass WAFs, and do their work undetected. The fact that DAST tools lack this capability distances them from real threat scenarios.
Sobele's New Definition of Noise
Sobele redefines the concept of "noise" in the cybersecurity industry in two dimensions:
First Dimension: False Positive Minimization
Yes, reports should not contain unnecessary findings. However, this should be achieved not by sacrificing real vulnerabilities, but through AI-powered analysis and evidence-based detection.
Second Dimension: WAF Silence (Stealth Testing)
A modern DAST tool should be able to operate by leaving zero suspicious requests on the target system. This means:
✅ Bypassing all modern WAFs including Cloudflare
✅ Performing high-risk tests like SQL Injection and XSS without receiving 403s
✅ Intelligently managing rate limiting mechanisms
✅ Overcoming CAPTCHA and bot protection
✅ Comprehensive scanning without leaving traces on the target system
Real-World Scenario: SQL Injection Behind Cloudflare
Consider an e-commerce site. Cloudflare protection is active, modern WAF rules are in place.
Scan with Invicti:
POST /api/products HTTP/1.1
...
id=1' OR '1'='1
Response: 403 Forbidden
WAF Log: Suspicious SQL Injection attempt detected
Result: Scan stopped, IP banned
Scan with Sobele:
POST /api/products HTTP/1.1
...
id=[payload hidden with bypass technique]
Response: 200 OK
Content: Database: ecommerce_prod, Tables: users, orders, payments
WAF Log: Clean, no suspicious activity
Result: SQL Injection detected, evidence produced
Conclusion: Noise Is Now Two-Dimensional
The cybersecurity industry must redefine what it expects from DAST tools. The "100% Signal, 0% Noise" slogan is no longer sufficient. The questions that should be asked are:
- ❓ Can you find real vulnerabilities? (False negative control)
- ❓ Can you overcome modern defense mechanisms? (WAF, CAPTCHA, Rate limiting)
- ❓ Do you create noise on the target system? (WAF logs, SOC alarms)
- ❓ Can you produce evidence? (Proof-based scanning)
- ❓ Do you understand modern web technologies? (SPA, mobile, API)
Sobele is a next-generation DAST platform that can answer "yes" to all of these questions. Noise is no longer just false positives; noise is also the digital footprints you leave in the WAF. And Sobele minimizes both types of noise while offering a world-class security testing experience.

No comments yet. Be the first to comment!